Which Of The Following Networking Devices Or Services Might Not Be Compatible With Vpn Connections
This browser is no longer supported.
Upgrade to Microsoft Edge to accept advantage of the latest features, security updates, and technical back up.
Configure and validate virtual network or VPN connections
This walkthrough provides footstep-by-step guidance to configure and validate diverse Azure VPN and virtual network deployments. Scenarios include transit routing, network-to-network connections, Edge Gateway Protocol (BGP), multisite connections, and point-to-site connections.
Azure VPN gateways enable flexibility in arranging nearly any kind of continued virtual network topology in Azure. For case, you tin connect virtual networks:
- Across regions.
- Betwixt virtual network types (Azure Resources Manager versus classic).
- Within Azure or within an on-premises hybrid environment.
- In unlike subscriptions.
Network-to-network VPN connection
Connecting a virtual network to some other virtual network (network-to-network) via VPN is similar to connecting a virtual network to an on-bounds site location. Both connectivity types apply a VPN gateway to provide a secure tunnel through IPsec and IKE. The virtual networks can be in the same or different regions, and from the same or dissimilar subscriptions.

If your virtual networks are in the same region, you might want to consider connecting them by using virtual network peering. Virtual network peering doesn't utilize a VPN gateway. It increases throughput and decreases latency. To configure a virtual network peering connectedness, select Configure and validate VNet Peering.
If your virtual networks were created through the Azure Resource Manger deployment model, select Configure and validate a Resource Manager VNet to a Resource Managing director VNet connectedness to configure a VPN connection.
If ane of the virtual networks was created through the Azure classic deployment model, and the other was created through Resource Manager, select Configure and validate a classic VNet to a Resource Manager VNet connectedness to configure a VPN connectedness.
Configure virtual network peering for two virtual networks in the same region
Earlier you start to implement and configure Azure virtual network peering, make sure that y'all run into the following prerequisites:
- The peered virtual networks must be in the aforementioned Azure region.
- The peered virtual networks must accept IP address spaces that don't overlap.
- Virtual network peering is betwixt ii virtual networks. In that location'due south no derived transitive relationship across peerings. For example, if VNetA is peered with VNetB, and VNetB is peered with VNetC, VNetA is not peered with VNetC.
When you meet the requirements, you can follow Tutorial: Connect virtual networks with virtual network peering by using the Azure portal to create and configure the peering.
To check the peering configuration, use the following method:
- Sign in to the Azure portal past using an account that has the necessary roles and permissions.
- In the box that contains the text Search resources at the height of the portal, blazon virtual networks. When Virtual networks appears in the search results, select it.
- In the Virtual networks blade that appears, select the virtual network for which yous want to create a peering.
- In the pane that appears for the virtual network, select Peerings in the Settings section.
- Select a peering and view the configuration results.
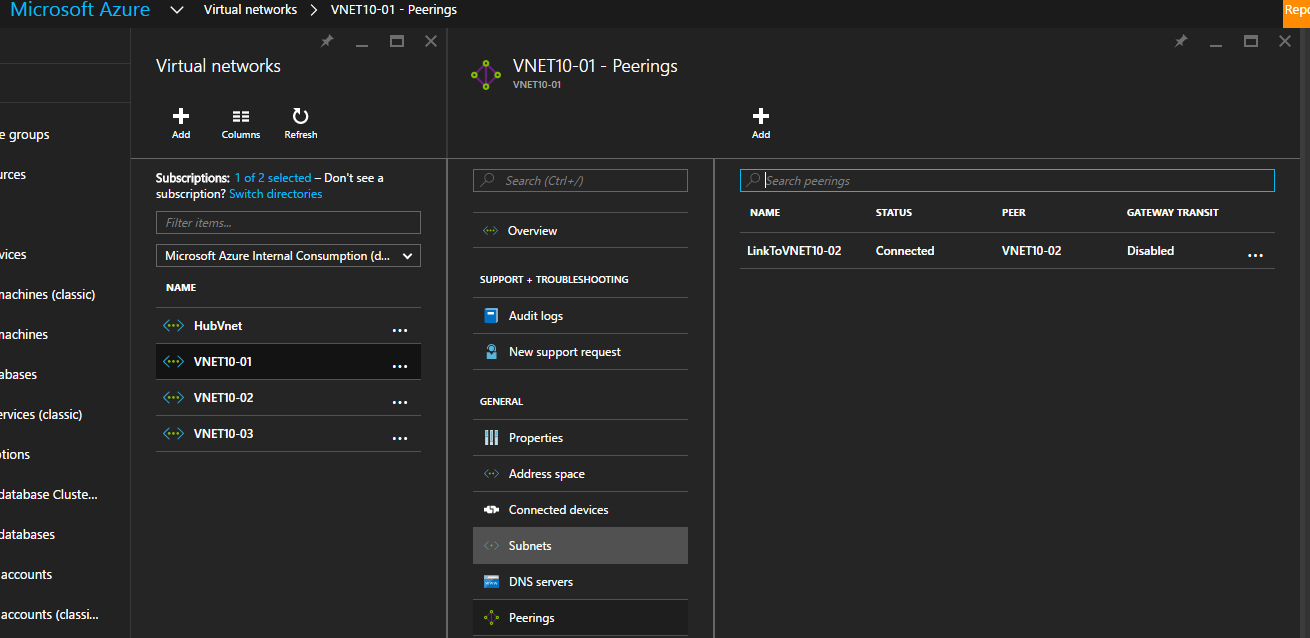
For Azure PowerShell, run the command Get-AzureRmVirtualNetworkPeering to go the virtual network peering. Here'southward an instance:
PS C:\Users\User1> Become-AzureRmVirtualNetworkPeering -VirtualNetworkName Vnet10-01 -ResourceGroupName dev-vnets Name : LinkToVNET10-02 Id : /subscriptions/GUID/resourceGroups/dev-vnets/providers/Microsoft.Network/virtualNetworks/VNET10-01/virtualNetworkPeerings/LinkToVNET10-0 two Etag : W/"GUID" ResourceGroupName : dev-vnets VirtualNetworkName : vnet10-01 ProvisioningState : Succeeded RemoteVirtualNetwork : { "Id": "/subscriptions/GUID/resourceGroups/DEV-VNET s/providers/Microsoft.Network/virtualNetworks/VNET10-02" } AllowVirtualNetworkAccess : True AllowForwardedTraffic : Fake AllowGatewayTransit : False UseRemoteGateways : Imitation RemoteGateways : null RemoteVirtualNetworkAddressSpace : null Connect a Resource Manager virtual network to another Resources Manager virtual network
You can configure a connexion from one Resources Manager virtual network to some other Resource Managing director virtual network directly. Or you can configure the connection past using IPsec.
Configure a VPN connection betwixt Resource Managing director virtual networks
To configure a connectedness between Resource Manager virtual networks without IPsec, see Configure a network-to-network VPN gateway connectedness by using the Azure portal.
To configure a connectedness with IPsec between ii Resources Manager virtual networks, follow steps one to v in Create a site-to-site connection in the Azure portal for each virtual network.
Note
These steps piece of work only for virtual networks in the same subscription. If your virtual networks are in unlike subscriptions, yous must employ PowerShell to brand the connection. See the PowerShell commodity.
Validate the VPN connection between Resource Managing director virtual networks
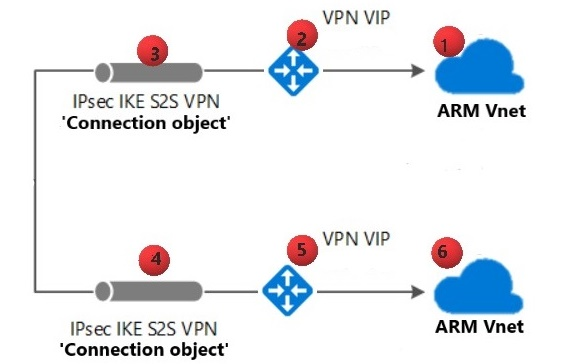
To check that your VPN connection is configured correctly, follow these instructions.
Annotation
The numbers after virtual network components in these steps stand for to the numbers in the preceding diagram.
- Make sure at that place are no overlapping address spaces in the connected virtual networks.
- Verify that the address range for the Azure Resource Managing director virtual network (1) is defined accurately in the Connection object instance (four).
- Verify that the accost range for the Azure Resource Manager virtual network (6) is defined accurately in the Connection object case (3).
- Verify that the pre-shared keys are matching on the connection objects.
- Verify that the Azure Resources Manager virtual network gateway VIP (2) is defined accurately in the Connexion object instance (4).
- Verify that the Azure Resource Manager virtual network gateway VIP (5) is defined accurately in the Connection object instance (3).
Connect a archetype virtual network to a Resource Manager virtual network
You can create a connexion between virtual networks that are in unlike subscriptions and in different regions. You can also connect virtual networks that already have connections to on-bounds networks, every bit long as you have configured the gateway type as route-based.
To configure a connectedness between a classic virtual network and a Resources Managing director virtual network, encounter Connect virtual networks from different deployment models by using the Azure portal.

To cheque the configuration when you connect a classic virtual network to an Azure Resource Director virtual network, follow these instructions.
Note
The numbers subsequently virtual network components in these steps represent to the numbers in the preceding diagram.
- Make sure there are no overlapping address spaces in the connected virtual networks.
- Verify that the address range for the Azure Resource Manager virtual network (6) is divers accurately in the classic local network definition (3).
- Verify that the address range for the classic virtual network (1) is divers accurately in the Azure Resources Manager Connection object instance (4).
- Verify that the classic virtual network gateway VIP (2) is defined accurately in the Azure Resources Manager Connection object instance (4).
- Verify that the Azure Resource Manager virtual network gateway (5) is defined accurately in the archetype Local Network Definition instance (3).
- Verify that the pre-shared keys are matching on both connected virtual networks:
- Classic virtual network: Local Network Definition (3)
- Azure Resource Manager virtual network: Connection object (4)
Create a point-to-site VPN connectedness
A bespeak-to-site (P2S in the post-obit diagram) configuration lets you create a secure connection from an private client computer to a virtual network. Bespeak-to-site connections are useful when you want to connect to your virtual network from a remote location, such as from habitation or a conference. They're likewise useful when you lot have only a few clients that demand to connect to a virtual network.
The point-to-site VPN connection is initiated from the client reckoner through the native Windows VPN customer. Connecting clients use certificates to authenticate.
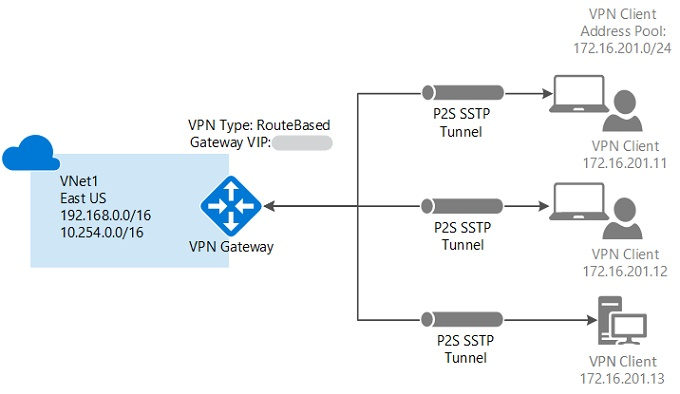
Indicate-to-site connections don't require a VPN device. They create the VPN connectedness over Secure Socket Tunneling Protocol (SSTP). You tin can connect a betoken-to-site connection to a virtual network by using various deployment tools and deployment models:
- Configure a point-to-site connection to a virtual network by using the Azure portal
- Configure a point-to-site connection to a virtual network by using the Azure portal (classic)
- Configure a point-to-site connection to a virtual network by using PowerShell
Validate your indicate-to-site connection
The article Troubleshooting: Azure indicate-to-site connection bug walks through common issues with point-to-site connections.
Create a multisite VPN connection
You can add a site-to-site (S2S in the following diagram) connectedness to a virtual network that already has a site-to-site connexion, indicate-to-site connexion, or network-to-network connection. This kind of connection is often chosen a multisite configuration.
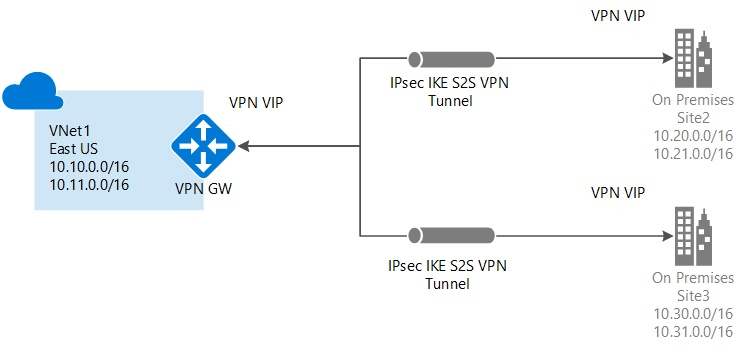
Azure currently works with ii deployment models: Resource Manager and archetype. The ii models aren't completely compatible with each other. To configure a multisite connection with unlike models, run into the following manufactures:
- Add a site-to-site connection to a virtual network with an existing VPN gateway connection
- Add a site-to-site connection to a virtual network with an existing VPN gateway connection (classic)
Configure transit routing
Transit routing is a specific routing scenario where you lot connect multiple networks in a daisy-chain topology. This routing enables resource in virtual networks at either end of the chain to communicate with i another through virtual networks in between. Without transit routing, networks or devices peered through a hub tin can't reach 1 some other.
Configure transit routing in a point-to-site connection
Imagine a scenario in which yous want to configure a site-to-site VPN connexion between VNetA and VNetB. You also desire to configure a bespeak-to-site VPN for the client to connect to the gateway of VNetA. Then, you desire to enable transit routing for the bespeak-to-site clients to connect to VNetB, which passes through VNetA.
This scenario is supported when BGP is enabled on the site-to-site VPN betwixt VNetA and VNetB. For more data, see Near betoken-to-site VPN routing.
Configure transit routing in an ExpressRoute connection
Azure ExpressRoute lets yous extend your on-premises networks into the Microsoft cloud over a dedicated private connection facilitated past a connectivity provider. With ExpressRoute, you can establish connections to Microsoft cloud services, such as Microsoft Azure, Microsoft 365, and Dynamics 365. For more information, see ExpressRoute overview.
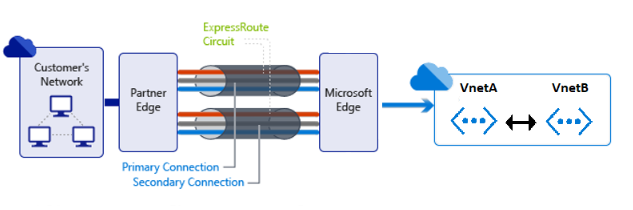
If y'all have ExpressRoute and site-to-site coexistence, transit routing isn't supported. For more than data, encounter Configure ExpressRoute and site-to-site by using PowerShell.
If you lot take enabled ExpressRoute to connect your local networks to an Azure virtual network, you can enable peering betwixt the virtual networks where you lot want to have transit routing. To let your local networks to connect to the remote virtual network, you must configure virtual network peering.
Note
Virtual network peering is bachelor only for virtual networks in the same region.
To check whether yous have configured transit routing for virtual network peering, follow these instructions:
- Sign in to the Azure portal by using an account that has the necessary roles and permissions.
- Create a peering between VNetA and VNetB as shown in the earlier diagram.
- In the pane that appears for the virtual network, select Peerings in the Settings department.
- Select the peering you lot want to view. So, select Configuration to validate that you have enabled Allow Gateway Transit on the VNetA network continued to the ExpressRoute circuit and Use Remote Gateway on the remote VNetB network not connected to the ExpressRoute circuit.
Configure transit routing in a virtual network peering connection
When virtual networks are peered, y'all can also configure the gateway in the peered virtual network as a transit point to an on-premises network. To configure a transit route in virtual network peering, run into Network-to-network connections.
Note
Gateway transit isn't supported in the peering relationship betwixt virtual networks created through unlike deployment models. Both virtual networks in the peering relationship must have been created through Resource Managing director for gateway transit to work.
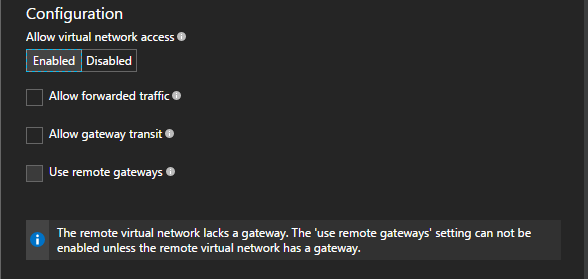
To check whether you have configured a transit route for virtual network peering, follow these instructions:
- Sign in to the Azure portal by using an account that has the necessary roles and permissions.
- In the box that contains the text Search resource at the top of the portal, blazon virtual networks. When Virtual networks appears in the search results, select it.
- In the Virtual networks blade that appears, select the virtual network for which you want to check the peering setting.
- In the pane that appears for the virtual network that y'all selected, select Peerings in the Settings section.
- Select the peering that y'all want to view. Validate that you have enabled Permit gateway transit and Utilise remote gateways under Configuration.
Configure transit routing in a network-to-network connection
To configure transit routing betwixt virtual networks, yous must enable BGP on all intermediate network-to-network connections by using the Resource Manager deployment model and PowerShell. For instructions, run into How to configure BGP on Azure VPN gateways by using PowerShell.
Transit traffic through Azure VPN gateways is possible through the classic deployment model, but that relies on statically defined address spaces in the network configuration file. BGP isn't yet supported with Azure virtual networks and VPN gateways through the classic deployment model. Without BGP, manually defining transit address spaces is error prone, and nosotros don't recommend it.
Note
You configure classic network-to-network connections by using the Azure classic portal, or by using a network configuration file in the classic portal. You can't create or alter a classic virtual network through the Azure Resources Manager deployment model or the Azure portal. For more than information on transit routing for archetype virtual networks, encounter the Microsoft Developer blog.
Configure transit routing in a site-to-site connexion
To configure transit routing between your on-bounds network and a virtual network with a site-to-site connection, you must enable BGP on all intermediate site-to-site connections by using the Resource Director deployment model and PowerShell. See How to configure BGP on Azure VPN gateways by using PowerShell for instructions.
Transit traffic through Azure VPN gateways is possible through the classic deployment model, but that relies on statically defined address spaces in the network configuration file. BGP isn't yet supported with Azure virtual networks and VPN gateways through the classic deployment model. Without BGP, manually defining transit address spaces is fault prone, and nosotros don't recommend it.
Note
You configure classic site-to-site connections past using the Azure classic portal, or by using a network configuration file in the classic portal. Y'all tin can't create or change a classic virtual network through the Azure Resource Managing director deployment model or the Azure portal. For more information on transit routing for classic virtual networks, see the Microsoft Developer weblog.
Configure BGP for a VPN gateway
BGP is the standard routing protocol used on the internet to exchange routing and reachability information between two or more than networks. When BGP is used in the context of Azure virtual networks, it enables the Azure VPN gateways and your on-bounds VPN devices, known equally BGP peers or neighbors. They commutation "routes" that will inform both gateways on the availability and reachability for those prefixes to get through the gateways or routers involved.
BGP can also enable transit routing among multiple networks by propagating routes that a BGP gateway learns from 1 BGP peer to all other BGP peers. For more data, run across Overview of BGP with Azure VPN Gateway.
Configure BGP for a VPN connection
To configure a VPN connectedness that uses BGP, see How to configure BGP on Azure VPN gateways by using PowerShell.
Enable BGP on the virtual network gateway by creating an autonomous system (AS) number for it. Basic gateways don't back up BGP. To check the SKU of the gateway, go to the Overview department of the VPN Gateway blade in the Azure portal. If your SKU is Bones, you have to alter the SKU (see Resizing the gateway) to VpnGw1.
Checking the SKU will cause 20 to thirty minutes of reanimation. As before long as the gateway has the correct SKU, you can add the AS number by using the Gear up-AzureRmVirtualNetworkGateway PowerShell commandlet. Afterwards you configure the As number, a BGP peer IP for the gateway will be provided automatically.
You must manually provide LocalNetworkGateway with an As number and a BGP peer address. You lot tin can prepare the ASN and -BgpPeeringAddress values by using either the New-AzureRmLocalNetworkGateway or the Set-AzureRmLocalNetworkGateway PowerShell commandlet. Some Every bit numbers are reserved for Azure, and y'all can't use them as described in About BGP with Azure VPN Gateway.
The connection object must take BGP enabled. You tin can set the -EnableBGP value to $True through New-AzureRmVirtualNetworkGatewayConnection or Set up-AzureRmVirtualNetworkGatewayConnection.
Validate the BGP configuration
To check whether BGP is configured correctly, you tin run the go-AzureRmVirtualNetworkGateway and get-AzureRmLocalNetworkGateway commandlets. Then you lot'll find BGP-related output in the BgpSettingsText part. For example:
{ "Asn": AsnNumber, "BgpPeeringAddress": "IP accost", "PeerWeight": 0 } Create a highly bachelor agile/active VPN connection
The key differences betwixt the active/active and agile/standby gateways are:
- You must create two gateway IP configurations with two public IP addresses.
- You lot must fix the EnableActiveActiveFeature flag.
- The gateway SKU must be VpnGw1, VpnGw2, or VpnGw3.
To achieve high availability for cross-bounds and network-to-network connectivity, you should deploy multiple VPN gateways and plant multiple parallel connections between your networks and Azure. For an overview of connectivity options and topology, come across Highly available cantankerous-premises and network-to-network connectivity.
To create active/active cantankerous-premises and network-to-network connections, follow the instructions in Configure active/agile S2S VPN connections with Azure VPN gateways to configure an Azure VPN gateway in active/active mode.
Note
- When yous add addresses to the local network gateway for BGP-enabled active/agile mode, add merely the /32 addresses of the BGP peers. If you lot add more addresses, they will be considered static routes and take precedence over BGP routes.
- You must utilize dissimilar BGP AS numbers for your on-bounds networks that are connecting to Azure. (If they're the same, you have to modify your virtual network Equally number if your on-premises VPN device already uses the ASN to peer with other BGP neighbors.)
Change an Azure VPN gateway type after deployment
You can't change an Azure virtual network gateway blazon from policy-based to road-based or the other fashion directly. You must showtime delete the gateway. After that, the IP address and the pre-shared key won't be preserved. Then you tin create a new gateway of the desired blazon.
To delete and create a gateway, follow these steps:
- Delete whatever connections associated with the original gateway.
- Delete the gateway by using the Azure portal, PowerShell, or classic PowerShell:
- Delete a virtual network gateway by using the Azure portal
- Delete a virtual network gateway past using PowerShell
- Delete a virtual network gateway past using PowerShell (archetype)
- Follow the steps in Create the VPN gateway to create the new gateway of the desired type and complete the VPN setup.
Note
This procedure will accept effectually 60 minutes.
Next steps
- Troubleshooting connectivity problems between Azure VMs
Feedback
Submit and view feedback for
Source: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-configure-vnet-connections
Posted by: garrisonvaccom.blogspot.com


0 Response to "Which Of The Following Networking Devices Or Services Might Not Be Compatible With Vpn Connections"
Post a Comment